Overview:
Threat actors have been using a Pokemon NFT card game website to distribute remote access software and use it to take control of victims’ devices.
Technical Summary:
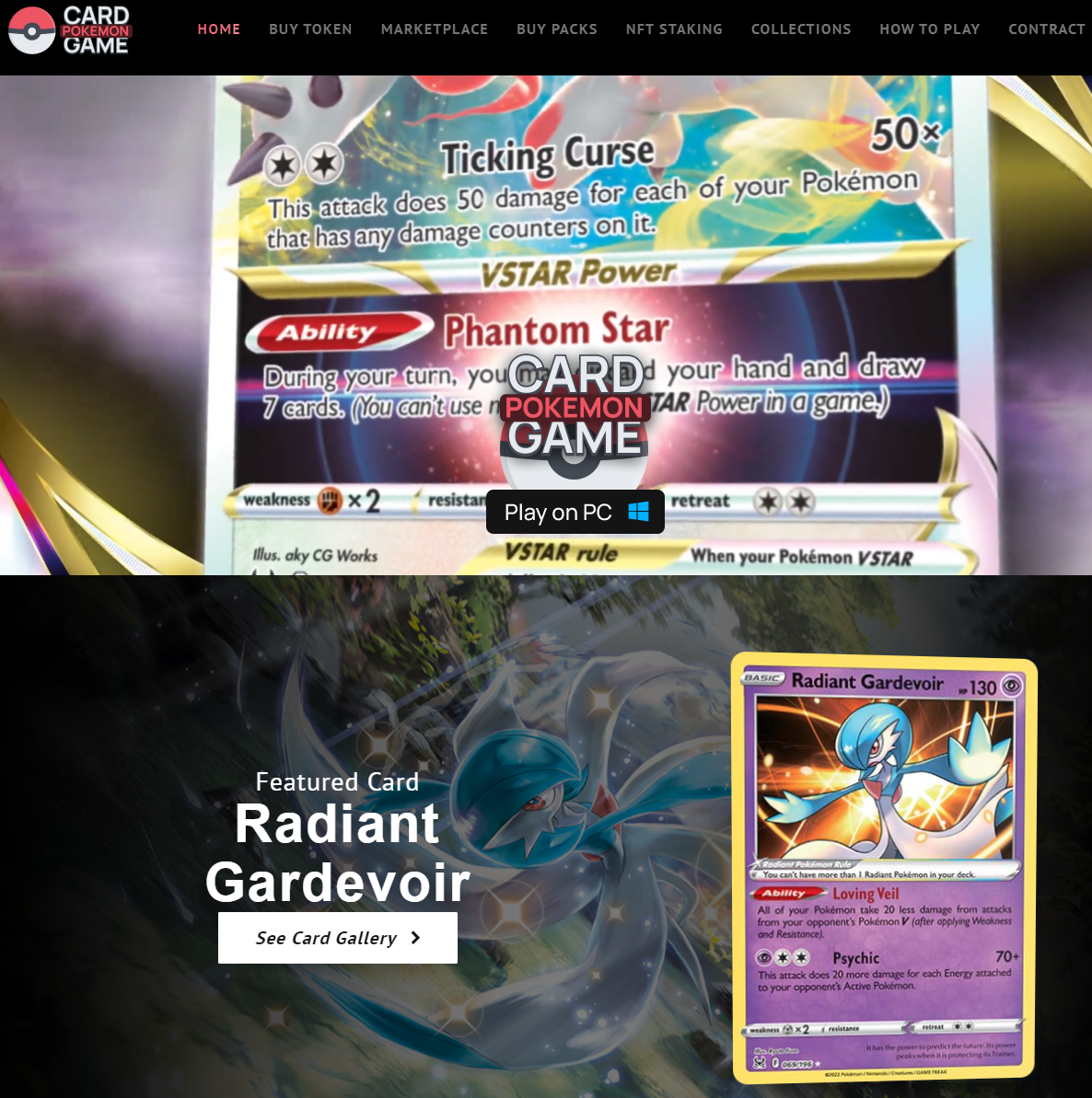
Many threat actors have been using a well-crafted Pokemon NFT game website to distribute the Netsupport remote access tool, which allows them to take over victims’ devices. The website that is being used to distribute the software is known as ‘pokemon-go[.]io’, as of now for the time being the website is still online.
The website is built around the Pokemon franchise, it offers users strategic fun together with NFT investment profits. The operators are able to easily draw in users due to the popularity of Pokemon and NFTs.
The threat actors get traffic to the site through spam, social media, and communication through private channels. Once the users are on the website they have the option to click the ‘Play on PC’ button.
If users click this button their computer downloads an executable that looks like a legitimate game installer, but in reality, the download installs the NetSupport remote access tool (RAT) on the victim’s system. Analysts at the company ASEC discovered the operation.
They reported that there was a second site used in the campaign at ‘beta-pokemoncards[.]io. But since the discovery, the website has been taken offline. The campaign was first seen in December 2022, earlier samples show that the same operators pushed a fake Visual Studio file instead of the Pokemon game.
Attack Tactics, Techniques & Procedures:
Command & Control (TA0011)
- Remote Access Software (T1219)
Exfiltration (TA0010)
- Exfiltration Over C2 Channel (T1041)
Privilege Escalation (TA0004)
- Exploitation for Privilege Escalation (T1068)
- Valid Accounts (T1078)
Defense Evasion (TA0005)
- Masquerading (T1036)
Collection (TA0009)
- Video Capture (T1125)
- Screen Capture (T1113)
Execution (TA0002)
- User Execution (T1204)
- Software Deployment Tools (T1072)
- Command & Scripting Interpreter (T1059)
- Boot or Logon Autostart Execution (T1547)
Reconnaissance (TA0043)
- Phishing for Information (T1598)
- Gather Victim Identity Information (T1589)
Impact (TA0040)
- Data Manipulation (T1565)
- Data Destruction (T1485)
Initial Access (TA0001)
- Valid Accounts (T1078)
- Phishing (T1566)
- Trusted Relationship (T1199)
- Exploitation of Public Facing Application (T1190)
Affected Assets & Organizational Impact:
Once the threat actors are able to get the remote software installed on the victim’s computer they can now remotely connect to it. Which allows them to steal data, install other malware, or even attempt to spread further on the network.
Even though NetSupport Manager is a legitimate software product it is commonly used by threat actors as part of their malicious campaigns. The app itself supports remote screen control, screen recording, system monitoring, remote system grouping for better control, and multiple connectivity options which include network traffic encryption.
All those things allow for a threat actor to steal valuable files off of someone’s computer, delete files, and overall destroy a victim’s computer as a whole. In 2020 and 2022 there were 2 incidents that revolved around downloading the NetSupport remote access software.
These included attackers using fake Cloudflare DDoS protection pages, and COVID-19-themed Excel files.
Mitigation and Response:
If installed the consequences can result in a broad and severe infection. The fake installer allows for unauthorized access to sensitive user data and downloading of more malware. This why it’s always recommended to check messages for suspicious details and to never click on links or download files from unknown senders. Also if a deal is too good to be true then most likely it is, to be on the safe side, do not click on those types of popups. Lastly, always download legitimate software from the company’s actual website rather than a third-party site/vendor.